Oracle Database Security Assessment Tool ( DBSAT) is a new security assessment product for Oracle databases. I heard it from Pedro Lopes ( (EMEA Field Product Manager at Oracle). He told to me give a try for this new product. Firsts, I was reluctant about the subject . But after I tried it; I saw that it is very practical tool to see your potential vulnerabilities at Oracle databases. It is very easy to install and you will get your report directly in a second.And It gives you time to think about your security bugs, you do not need to think about how you can install and start the product.
Overview of the Product
DBSAT runs on a Oracle database server to analyze database security. It is a command line program.It runs queries to collect information about the Oracle database and database server For each database you have install and run it.
It has two parts;
DBSAT collector; runs queries to collect data
DBSAT reporter: Produces report from collected data and gives recommendation on different formats.
Installation
I made my installation on a Oracle Vm machine Linux 7 and I used Oracle 12c database.
Create a directory to work on DBSAT files
[oracle@ol7 ~]$ mkdir /home/oracle/dbsat
[oracle@ol7 ~]$ cd /home/oracle/dbsat
Download dbsat.zip file from Oracle Metalink and put this file to the dbsat directory.
Oracle Database Security Assessment Tool (DBSAT) (Doc ID 2138254.1)
And Install the dbsat.zip
[oracle@ol7 dbsat]$ unzip dbsat.zip -d /home/oracle/dbsat
Directory Listing should be like that;
[oracle@ol7 dbsat]$ ls -lrt
total 520
-r-xr-xr-x. 1 oracle oinstall 24757 Sep 27 20:55 sat_analysis.py
-r-xr-xr-x. 1 oracle oinstall 9198 Oct 7 19:09 dbsat.bat
-r-xr-xr-x. 1 oracle oinstall 229245 Oct 21 19:09 sat_reporter.py
-r-xr-xr-x. 1 oracle oinstall 9039 Oct 21 19:09 dbsat
-r-xr-xr-x. 1 oracle oinstall 42135 Oct 27 21:11 sat_collector.sql
-rwxr-x—. 1 oracle dba 198362 Mar 5 10:09 dbsat.zip
drwxr-xr-x. 2 oracle oinstall 4096 Mar 5 10:12 xlsxwriter
Running DBSAT Collector
you can run DBSAT collector with a user which needs below privileges.
CREATE SESSION
SELECT on SYS.REGISTRY$HISTORY
Role SELECT_CATALOG_ROLE
Role DV_SECANALYST (if Database Vault is enabled)
Role AUDIT_VIEWER (12c only)
Role CAPTURE_ADMIN (12c only)
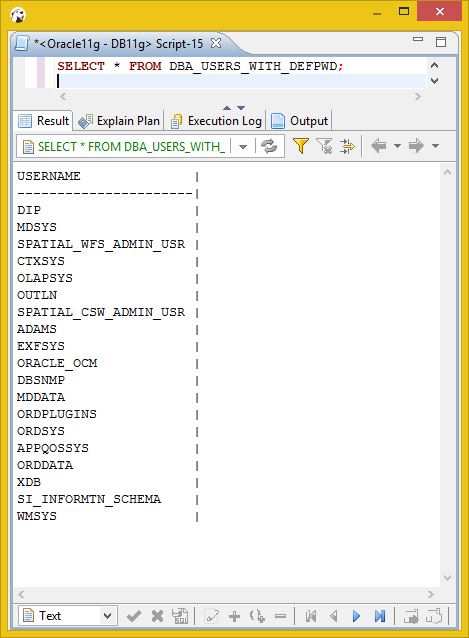
SELECT on SYS.DBA_USERS_WITH_DEFPWD (11g and 12c)
SELECT on AUDSYS.AUD$UNIFIED (12c only)
You can create a special user with these privileges or you can use a highly privileged user like I use .
First set the Oracle environments
Run the DBSAT collector with sys user like below; Note my DB name is DB3
At the end of the data collection; you need to enter a password to protect the collected data. Do not forget this password you will enter the same password to produce report.
[oracle@ol7 ~]$ cd /home/oracle/dbsat
[oracle@ol7 dbsat]$ ./dbsat collect “sys/manager as sysdba” DB3
DBSAT Collector completed successfully.
Calling /u01/app/oracle/product/12.1.0.2/db_1/bin/zip to encrypt DB3.json…
Enter password:
Verify password:
adding: DB3.json (deflated 86%)
zip completed successfully.
Running DBSAT Reporter
DBSAT reportor onyl needs Python 2.6 or later to run.
at the end of the report , the reporter will zip the files with a password
[oracle@ol7 ~]$ cd /home/oracle/dbsat
[oracle@ol7 ~]$ ./dbsat report DB3
Calling /usr/bin/zip to encrypt the generated reports…
Enter password:
Verify password:
adding: DB3.txt (deflated 79%)
adding: DB3.html (deflated 84%)
adding: DB3.xlsx (deflated 3%)
zip completed successfully.
At the end of the process you will get two files like below.
DB3.zip consists of collected data and DB3_report.zip contains reports.
[oracle@ol7 dbsat]$ ls -lrt DB3*
-rw——-. 1 oracle oinstall 34030 Mar 5 16:12 DB3.zip
-rw——-. 1 oracle oinstall 61746 Mar 5 16:17 DB3_report.zip
Report Sample
Now copy the report file to your PC and open it

The report contains below parts

You can go to any parts from the summary part.
I added my report as an Excel file and pdf file
db3-oracle-database-security-risk-assessment
db3
Documentation
Some Documents about the DBSAT.
Oracle Database Security Assessment Tool (DBSAT) (Doc ID 2138254.1)
Database Security Assessment Tool User Guide
https://docs.oracle.com/cd/E76178_01/SATUG/toc.htm#SATUG-GUID-C7E917BB-EDAC-4123-900A-D4F2E561BFE9
https://stefanpanek.wordpress.com/2017/02/04/oracle-dbsat-first-experience/
,












Reply