Dynamic Data Masking in SQL Server 2017
Dynamic Data Masking ( DDM) masks the selected column data during query execution. Simply masking is applied to the query results. DDM hides sensitive data from a central location. For example you can hide some portion of credit card information or whole maiden surname information from the users.
Actually DDM is not a full solution to secure sensitive data in the database. Because It is possible for malicious users to guess the masked date by running some special queries like below.
Select Customer_id, salary from Employee where Salary=1000;
Select Customer_id, salary from Employee where Salary=1001;
Select Customer_id, salary from Employee where Salary=1002;
In that case; we should audit the database to find such attacks.
There are four type of masks available
Default Masking : This is Full masking . For strings it uses XXXX and for number it uses 0 to mask data values. For example;
ALTER COLUMN MaidenSurname ADD MASKED WITH (FUNCTION = ‘default()’)
Email Masking : This method of masking masks first letter of email address like below;
ALTER COLUMN Email ADD MASKED WITH (FUNCTION = ’email()’)
Random Masking; Randomly masks any numeric data within specified range
ALTER COLUMN Salary ADD MASKED WITH (FUNCTION = ‘random(1, 12)’)
Custom String: It masks some portion of the data by padding string in the middle.
ALTER COLUMN Customer_surname ADD MASKED WITH (FUNCTION = ‘partial(1,”XXXXXXX”,0)’)
Now I will give you an example ; In this example I will create a table with masked columns, and then after adding some rows into this table we will query the table and check the results.
Let’s create the table in my Sample01 database. In this table we created three masked columns and selected the table with the user sa. This user has sysadmin privilege therefore It can see the value of masked columns.
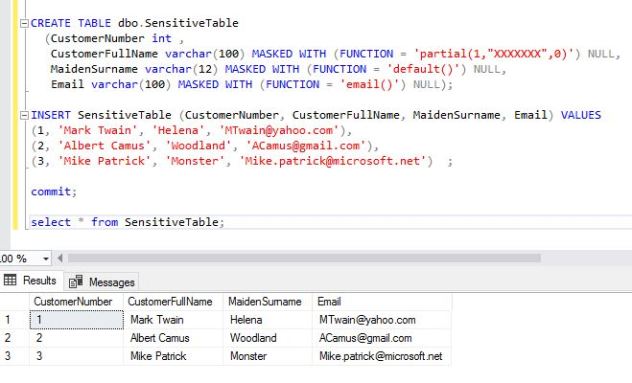
Normal user with the the select privilege of this table can not see the value of masked columns as you see in the below picture.
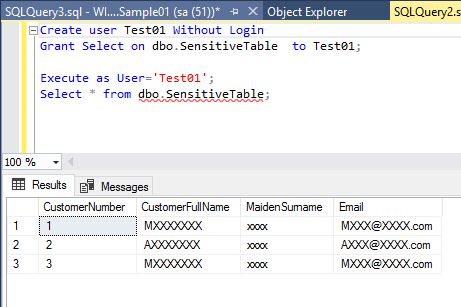
Only the user with UNMASK privilege can see the value of masked columns.

In order to select the definitions of masked column information we should query sys.masked_columns view by joining sys.tables views.
SELECT a.name,
b.name,
a.is_masked,
a.masking_function
FROM sys.masked_columns a,
sys.tables b
WHERE a.object_id = b.object_id
AND a.is_masked = 1;
In order to drop the definition of masking column we use ALTER TABLE command .

If you want ; you can change the masking type of a column with ALTER TABLE command.

I think that ; this note should be a good starting point for you to learn DDM in SQL Server 2017.
Y. Anil Akduygu




















Adem 14:12 on 27 March 2019 Permalink |
Thanks for sharing, it is very clear and helpful 🙂
LikeLike